web application security solutions
Table of Contents
1. Introduction to Web Application Security Solutions
2. The Importance of Web Application Security
3. Common Web Application Security Threats
3.1 Cross-Site Scripting (XSS)
3.2 SQL Injection
3.3 Cross-Site Request Forgery (CSRF)
3.4 Brute Force Attacks
4. Understanding Web Application Security Solutions
4.1 Web Application Firewalls (WAF)
4.2 Secure Coding Practices
4.3 Regular Security Audits and Penetration Testing
5. Choosing the Right Web Application Security Solution
5.1 Assessing Your Security Needs
5.2 Considering Budget and Scalability
5.3 Evaluating User-Friendliness
6. Top Web Application Security Solutions in the Market
6.1 Acunetix
6.2 Imperva WAF
6.3 Fortify
6.4 Veracode
6.5 Cloudflare WAF
7. Implementing Web Application Security Solutions
7.1 Step-by-step Deployment Process
7.2 Integrating Security into Development Lifecycle
7.3 Employee Training and Awareness
8. The Future of Web Application Security
9. Conclusion
Best Hosting
Web Application Security Solutions: Protecting Your Online Presence
In today’s digital age, web applications have become an integral part of our daily lives. From online shopping to social media, we rely heavily on web applications for various tasks. However, with the increasing use of web applications, the risk of cyberattacks and data breaches has also grown significantly. To safeguard your online presence and protect sensitive information, it is crucial to implement robust web application security solutions.
The Importance of Web Application Security
Web application security is not just an option; it is a necessity. A single security breach can have severe consequences, including financial losses, damaged reputation, and legal repercussions. By investing in the right security solutions, individuals and businesses can safeguard their data and ensure the smooth functioning of their web applications.
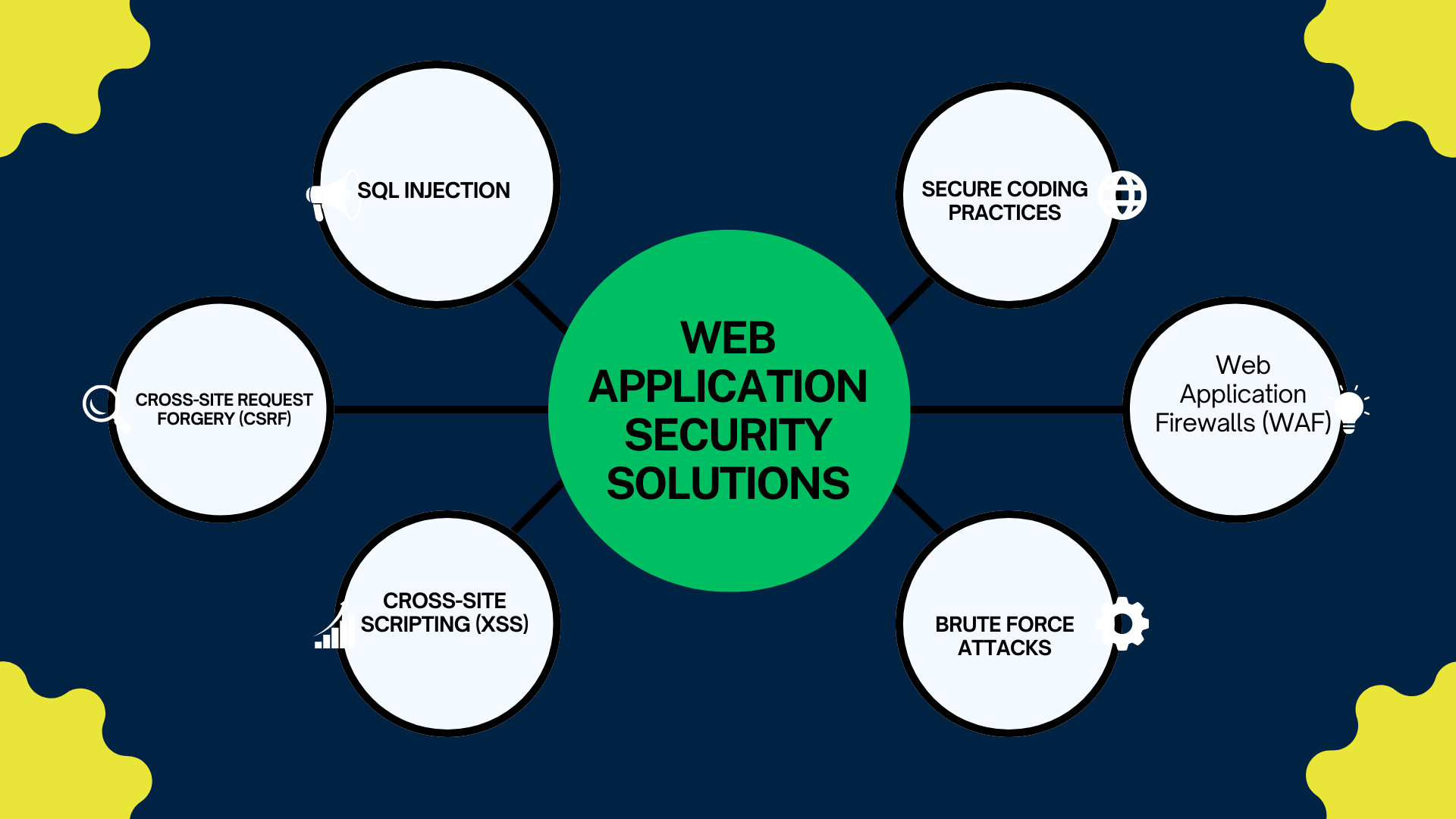
Common Web Application Security Threats
Various cyber threats target web applications daily. Understanding these threats is essential in devising effective security measures.
Cross-Site Scripting (XSS)
XSS attacks involve injecting malicious scripts into web pages viewed by other users. These scripts can then steal sensitive data or even hijack user sessions. Implementing proper input validation and output encoding can help mitigate this risk.
SQL Injection
SQL injection exploits vulnerabilities in web applications’ databases. Attackers can insert malicious SQL queries to gain unauthorized access to databases. Web developers should use parameterized queries and prepared statements to prevent SQL injection.
Cross-Site Request Forgery (CSRF)
In CSRF attacks, hackers trick users into executing unwanted actions on web applications they are logged into. Token-based authentication and the SameSite attribute can help prevent CSRF attacks.
Brute Force Attacks
In brute force attacks, hackers attempt to crack passwords through repeated login attempts. Employing strong password policies and account lockout mechanisms can enhance security against such attacks.
Understanding Web Application Security Solutions
To defend against these threats, web application security solutions play a vital role. Let’s explore some of the essential security measures:
Web Application Firewalls (WAF)
A WAF acts as a barrier between web servers and potential threats. It filters and monitors incoming traffic, blocking malicious requests while allowing legitimate ones.
Secure Coding Practices
Developers must follow secure coding practices to build robust web applications. This includes input validation, avoiding code vulnerabilities, and ensuring data encryption.
Regular Security Audits and Penetration Testing
Regular security audits and penetration testing help identify vulnerabilities before malicious actors exploit them. Periodic assessments keep web applications up-to-date and secure.
Choosing the Right Web Application Security Solution
With numerous security solutions available, selecting the one that best fits your needs is crucial.
Assessing Your Security Needs
Identify your web application’s specific security requirements based on its complexity and sensitivity of data processed.
Considering Budget and Scalability
Choose a solution that aligns with your budget and can scale as your web application grows.
Evaluating User-Friendliness
The usability of the security solution is essential for efficient implementation and management.
Top Web Application Security Solutions in the Market
Several reputable web application security solutions can fortify your defenses against potential threats.
Acunetix
Acunetix offers a comprehensive vulnerability scanning tool that identifies and resolves security flaws in web applications.
Imperva WAF
Imperva WAF provides robust protection against various attacks, including OWASP Top 10 threats, and can be deployed both on-premises and in the cloud.
Fortify
Fortify offers static and dynamic application security testing (SAST and DAST) solutions, ensuring early detection of vulnerabilities in the development process.
Veracode
Veracode’s platform includes automated security testing to quickly identify and fix flaws in web applications.
Cloudflare WAF
Cloudflare WAF provides a cloud-based web application firewall with high-performance and global coverage.
Implementing Web Application Security Solutions
The successful implementation of security solutions requires a systematic approach.
Step-by-step Deployment Process
Follow a well-defined deployment process, including planning, testing, and post-deployment monitoring.
Integrating Security into Development Lifecycle
Incorporate security practices throughout the web application development lifecycle to address vulnerabilities from the early stages.
Employee Training and Awareness
Ensure that employees are well-informed about security measures and potential threats to prevent human errors.
The Future of Web Application Security
As technology evolves, web application security will face new challenges and opportunities. Emphasizing continuous improvement and staying updated on emerging threats will be crucial.
Conclusion
Web application security solutions are indispensable in today’s cyber threat landscape. Safeguarding your web applications protects not only your data but also the trust of your users and customers. By adopting the right security measures and implementing them effectively, you can ensure a safe and seamless online experience for all stakeholders.
FAQs
1. What is the primary goal of web application security solutions?
Web application security solutions aim to protect web applications from cyber threats and prevent data breaches.
2. Can I rely solely on secure coding practices to secure my web application?
While secure coding practices are crucial, combining them with other security measures provides a more robust defense.
3. How often should I conduct security audits and penetration testing?
Regular security audits and penetration testing should be performed at least annually or whenever significant changes are made to the web application.
4. Are cloud-based web application security solutions as effective as on-premises solutions?
Yes, cloud-based solutions can be just as effective, offering scalability, flexibility, and global coverage.
5. **What is the future outlook for web application security?**
The future of web application security will involve advanced technologies like AI and machine learning to proactively detect and prevent emerging threats.